HOW CAN YOU PROTECT WHAT YOU CAN'T SEE?
Do You Know What Your Assets Are?
Over the last decade, the rise of third-party solutions and digital platforms has expanded organizational attack surfaces, opening blind spots for vulnerabilities, exposures, and malicious activity to persist undetected. As a result, the digital boundaries of your organization have become much more blurred, making it harder to see where you may be exposed. Without continuous security monitoring, these blind spots can quickly turn into entry points for threat actors - especially as new threats now emerge faster than ever compared to just a few years ago.
Security Vulnerabilities
Detect, identify, and accurately prioritize both network and web application security vulnerabilities, misconfigurations, and exposures before threat actors can exploit them.
Threat Intelligence
Monitor data breaches and phishing campaigns, track indicators of compromise (IoCs) and real-time trends, and scan the dark and deep web to stay ahead of emerging threats.
Oversight & Insights
Stay in control with real-time alerts delivered to email, Slack, and ITSM solutions, alongside clear reports and seamless integrations with your existing security tools.
ThreatLeap
Complete Security Monitoring with Built-in Cyber Intelligence
ThreatLeap is a SaaS solution that continuously monitor your organization's digital posture to detect vulnerabilities, exposures and misconfigurations. Powered by AI and cutting-edge threat identification technology, it provides real-time alerts along with actionable threat and risk intelligence. When it comes to staying secure and one step ahead - you've come to the right place.
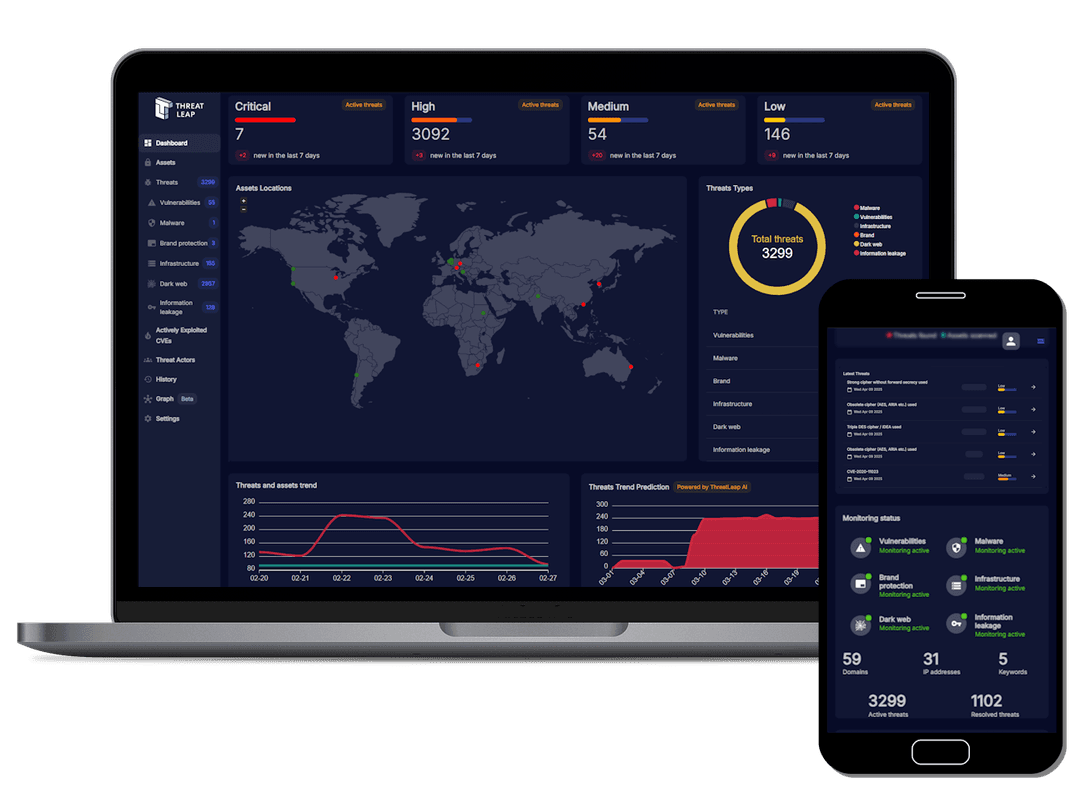
We Deliver Network & Web Application Security Vulnerability Monitoring ...
ThreatLeap provides continuous monitoring to identify weaknesses before threat actors can exploit them. It scans across both infrastructure and applications. With prioritized insights and actionable intelligence, your team can remediate faster and reduce exposure.

Network Security Vulnerability Monitoring
Security vulnerabilities, often tracked through Common Vulnerabilities and Exposures (CVEs), represent known weaknesses in operating systems, software packages, and third-party components. Our solution continuously monitors published CVEs, correlates them with your digital posture, and prioritizes them based on severity and exploitability.

Web Application Security Vulnerability Monitoring
Web applications are a prime target for threat actors, and issues such as SQL injection, Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF) remain among the most exploited ones. Using dynamic application security testing (DAST), our platform performes real-world security testing to uncover vulnerabilities in running web applications and APIs.
... Alongside First-Class Cyber Intelligence ...
ThreatLeap delivers precise, 24/7 cyber risk intelligence about your organization. We monitor your digital footprint and detect what threat actors could exploit - and what they already know about you. Our platform collects, analyzes, and delivers actionable insights across the threat landscape in multiple ways:
Public Infrastructure Monitoring and Content Crawling
ThreatLeap scans your digital infrastructure to detect vulnerabilities, misconfigurations, and exposed assets in real time. Our 24/7 monitoring technology uncovers security gaps, such as dangerous open ports, out-of-date software, sensitive unprotected files, and malware. We monitor the digital environment, third-party integrations and public services to ensure complete visibility.
Dark Web and Deep Web Monitoring and Scraping
Threat actors trade stolen data and hacking tools on underground forums and hidden networks. ThreatLeap monitors the dark and deep web to detect mentions of your organization, leaked credentials and other sensitive data. Our AI-driven monitoring tracks cybercriminal activity and provides real-time alerts on emerging threats.
Global Trends and Threat Actors Database
Cyber threats evolve daily, and staying informed is crucial. ThreatLeap tracks global attack trends, mapping threat actors, their tactics and their targets. Our database provides insights into ransomware, phishing, malware, indicators of compromise and the latest vulnerabilities and exploits.
... With Features Built for the Front Lines of Cyber Defense.
Threat actors move fast. You need to move faster. ThreatLeap uncovers emerging threats, vulnerabilities, dark web exposure, and more - giving you the intelligence to defend your digital assets. Stay ahead of compliance with the EU's NIS2 Directive and DORA Regulation, while we help you tackle evolving cyber threats with precision and speed.
SECURITY VULNERABILITY IDENTIFICATION
Identifying security vulnerabilities that could be abused and exploited by threat actors, APTs, foreign state-sponsored threat actors and malicious individuals to deploy ransomware or gain a foothold into your internal network.
WEB APPLICATION VULNERABILITY IDENTIFICATION
Using dynamic application security testing (DAST), our platform continuously identifies vulnerabilities across web applications and APIs - including OWASP Top 10 issues like SQLi, XSS and CSRF - correlates them with runtime evidence, and prioritizes by severity and exploitability.
NETWORK INFRASTRUCTURE MONITORING
Detection and enumeration of external public internet-facing network infrastructure in order to keep track of digital assets inventory, discovery of potentially forgotten out-of-date or end-of-life (EOL) assets which can pose a danger to organization’s defenses.
MALWARE SCANNING AND MONITORING
ThreatLeap continuously monitors organization’s websites, both main domains and subdomains for indicators of drive-by download attacks, malvertising, malicious software or hacked/compromised websites.
GDPR/PCI-DSS VIOLATIONS INSPECTION
Continuous and automatic monitoring of organization’s publicly-facing services for unintentional regulatory violations and data leaks (SSN, Credit Card, etc.) and other PII on publicly accessible digital assets of the organization.
BRAND PROTECTION AND SUPERVISION
Keeping an eye on real-time phishing campaigns and phishing domains that are targeted against your organization. Alerting an organization, so it can promptly alert employees, clients or users and take necessary steps to shut them down.
SECURITY BREACHES INSPECTION
Constantly looking at your organization’s members’ credentials, such as usernames and passwords disclosed or leaked in some of the third-party security breaches and leaks.
DARK/DEEP WEB INTELLIGENCE
Keeping an eye on threat actors to see if they are sharing or selling some information about your organization on the dark web and deep web forums and marketplaces. Alerting you if they have some sensitive information or if your organization is breached.
REAL TIME TRENDS INTELLIGENCE
Monitoring and informing you about the latest techniques, tactics and tricks that threat actors are pulling on organizations in specific industries on a daily basis. Tracking nearly a thousand of the most popular and dangerous threat actors and their motives.
INDICATOR OF COMPROMISE DETECTION
Our continuously updated database of known-bad IPs ships in firewall-ready formats for automated ingestion, enabling on-prem and cloud controls to proactively block malicious traffic, cut time-to-detect, and reduce false positives while shrinking your attack surface.

